Pentests Protect Your IT Systems!
If attackers manage to penetrate your systems, this can mean the loss of data and trust. Our experienced IT security experts help you with a pentest to protect your web applications, mobile apps and systems from real threats and implement risk mitigation.
Effective Solution for High IT Security
The Pentest
Benefit from many years of experience! Pentests are planned, executed and evaluated by our specially trained cyber security engineers according to recognized IT security standards.
Reasons for a Pen Test
That's why you Should Perform a Pen Test with turingpoint!
Our experienced IT security consultants uncover vulnerabilities before a real hacker can exploit them. Reduce remediation costs, network downtime and preserve your company's image with the accompanying customer loyalty. Pen tests enable compliance with security regulations defined, for example, within the framework of IT-Grundschutz in an Information Security Management System (ISMS). There are several variables involved in our pricing.
- Extensive Reporting Format + Free One-time Retest
- Our report is prepared according to recognized standards and contains, among other things, a management summary, a vulnerability overview, details of the vulnerability, and remediation steps. The assessment of the findings is based on the CVSS 3.0 standard. The one-time retest is free of charge with us.
- Certification as Proof for Your Customers
- Use our comprehensive security certificate to prove to customers the high security level of your applications and infrastructures. Successful accreditation is preceded by a cloud assessment or pen test.

Manual Execution on Site or Remotely
Penetration Tests from turingpoint are Handmade!
Automated vulnerability scanners cannot replace full penetration tests. It would be negligent to believe that a vulnerability scan provides a good level of security or protection against a real attacker! We offer remote or on-site during the execution.
- 5 Reasons Why you should Perform Pentesting
The surest way to measure your security level is to examine how it can be hacked. A pentest offers the possibility to test your system's resistance (Cyber Resilience) against external and internal hacking attempts. To the article
- IT Security Situation in Germany in 2024
While it may sound counterintuitive, spending money on pentests will actually save your organization a significant amount of money. Pentests highlight the areas of greatest vulnerability, which will inform you where to spend your IT security budget most effectively. Without penetration testing to guide you, it would be necessary to spend more money on a wider range of aspects. BSI Situation Report
- Annual Number of Data Breaches and Records Disclosed
There's no doubt that penetration tests play a critical role in protecting your business and its valuable assets from potential intruders. However, the benefits of pentesting go far beyond network and data security. Source Statista
Expertise around Cyber Security
Boutiqe Consulting with Expertise in Cyber Security
We offer all services in various complexities and recognized standards.
- Testing of All Systems
- Basically, we classify penetration tests in web applications, mobile apps and infrastructures. However, the requirements are evaluated individually for each project. Optionally, we perform a Darknet Intelligence Assessment.
- Disruptive Technologies
- Experience with disruptive cloud technologies such as AWS, Google Cloud Platform or Microsoft Azure.
- Own Research + Development
- Proprietary and constantly updated scanner software in addition to common commercial tools. Additional development of security solutions for automated scanning and vulnerability management.
- External Accreditation According to ISO 27001
- Especially as an IT security service provider and software developer, an external audit of our ISMS is of great importance to communicate trust.

Process Steps of a Successful Penetration Test
Penetration Test Procedure
The pentest we perform is an agile process and is carried out in close consultation with the customer.
Kick-off
During a joint kick-off meeting, the framework conditions to be tested are specified, necessary user accounts and access paths are coordinated, contact persons and escalation paths are defined, and the pentest is planned together in detail.
Manual & Automated Research
Our security engineers try to gather as much information as possible. Based on this information, analysis strategies are developed to identify possible attack vectors. These attack vectors are then examined for vulnerabilities in extensive tests.
Manual Exploitation
Here, an attempt is made to exploit the identified vulnerabilities to gain access to the target systems. In the process, our pentester writes new exploits or uses existing ones, depending on the service or technical environment in question. Potential vulnerabilities can turn out to be false positives here. Only verified vulnerabilities are included in the final report and classified according to their criticality according to CVSS 3.0.
Report
We have developed a comprehensive report format that provides optimal insight into our work and its results. This consists of a business risk analysis, management summary and a comprehensive test and vulnerability description. The criticality of the vulnerabilities and recommendations for action are described in detail therein.
Final interview & Certification (optional)
In the final meeting, all critical points in the results report are discussed and all questions are clarified. Finally, we are happy to present you with a certificate as proof for your customers.
Remediation (Optional)
When the analysis is complete, then the remediation of the identified vulnerabilities takes place on your part. Our evaluations provide you with detailed recommendations about the vulnerability in question. If needed, our security engineers can provide extensive remediation assistance.
Free review (Optional)
We are happy to review the security weaknesses again to ensure that the defense mechanisms have been implemented correctly. It is important to us that our recommendations are implemented, which is why this process activity is always free of charge.
Penetration Test Abstraction Levels for All Technologies
Range of Services for IT Security Penetration Testing
Basically, we classify IT security penetration tests into three types, which, however, can also be compiled individually for each project.
Web Applications
A web pentest focuses exclusively on web technologies. Web applications and APIs have wide-ranging permissions that offer a variety of attack vectors and are mostly tied to the infrastructure.
Mobile Apps
Our mobile app pentesters have a background in network and web pentesting, a quality necessary for mobile app pentesting because almost every app communicates with a backend system.
Infrastructures
The pentest for critical IT infrastructures (KRITIS) tests the security of e.g. server systems, VPN systems, WLAN networks and firewalls. As a basis for secure applications, the system as well as the network infrastructure must not be neglected.
Definition and Explanation
What is Penetration Testing?
Penetration testing or pentesting for short are simulated attacks from external or internal sources to determine the security of web applications, apps, networks and infrastructures and uncover any vulnerabilities. By methodically and manually validating the effectiveness of security controls, we identify points of attack in your systems so they can be remediated early. Any security issues identified are presented to you along with an impact assessment, risk mitigation proposal or technical solution.
Range of Services for Cyber Security
Further useful Services within the Scope of an IT Security Audit
- Cloud Security
- Due to the increasing complexity of cloud infrastructures, many services are misconfigured. We help you identify and eliminate misconfigurations and their effects.
- Phishing Simulation
- A spear phishing simulation is used to increase the detection ability of employees. We help you to sensitize your employees and thus strengthen the last barrier.
- Static Code Analysis
- Static code analysis, also known as source code analysis, is typically performed as part of a code review and takes place during the implementation phase of a Security Development Lifecycle (SDL).
- Red Teaming
- Red Teaming is used to test an organization's detection and response capabilities. Our Red Team tries to access sensitive information in every possible way and as undetected as possible.
Penetration Testing as a Service (PTaaS)
Penetration Tests on the Platform turingsecure.
We offer comprehensive vulnerability management for customers, partners, penetration testers and IT security consultants. Use our software products to also get the best technologies and reporting tools on the market.
Application Level Security Measures
Comprehensive Solutions for your Application Security
With our comprehensive and intuitive platform, you can now map the entire security process of your applications. To the penetration testing platform
- Continuous Application Security Testing
- Continuous Security Application Testing (CAST) ensures that applications are tested for vulnerabilities in a regulated cycle. Our methodology allows direct integration into the agile development process and thus enables a high continuous security level.
- On-Demand Penetration Testing
- Application penetration testing is scaled as needed to meet the more complex requirements. For a sophisticated application, a quick and manual penetration test can be performed to identify vulnerabilities in the business logic of your application.
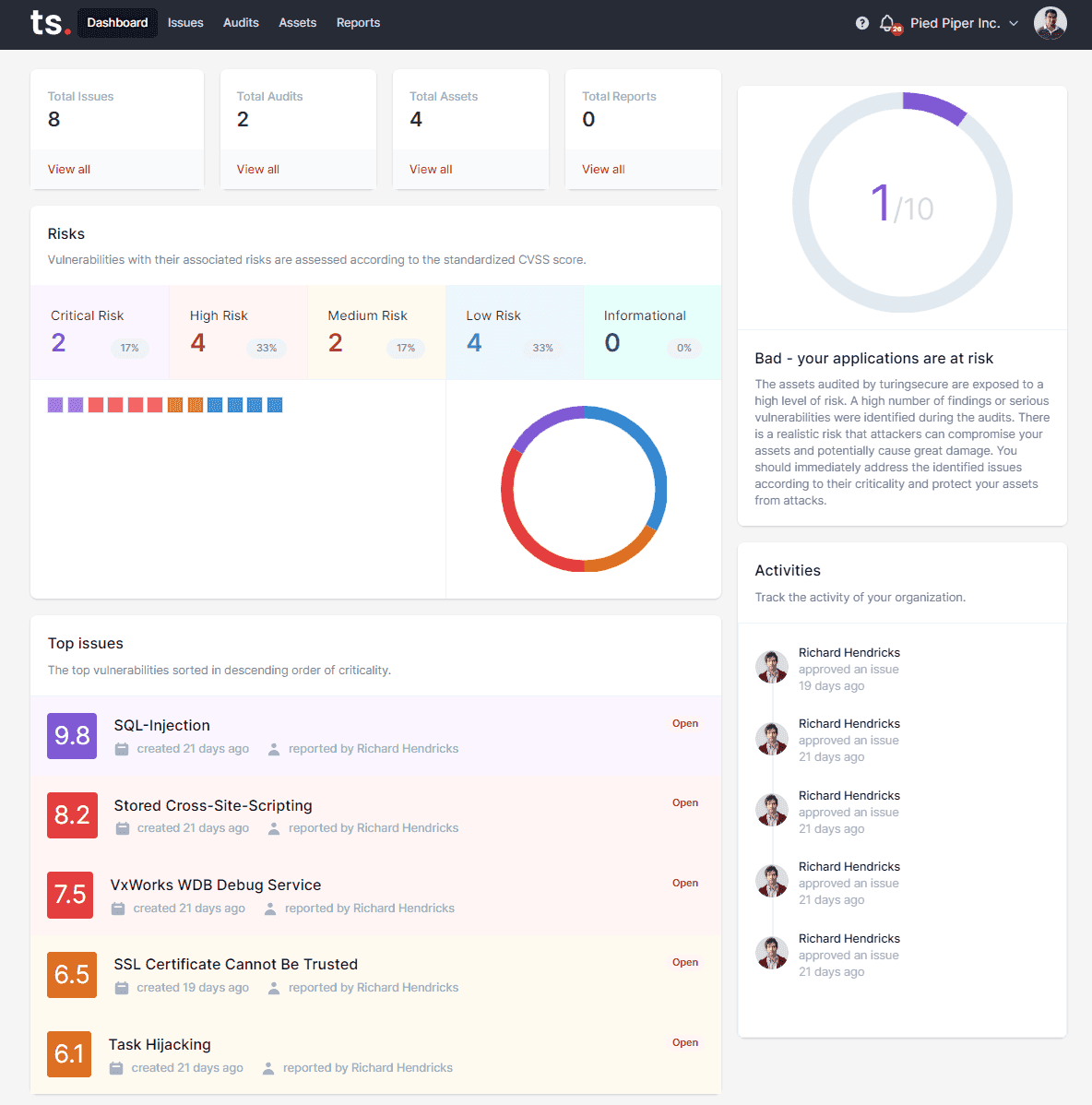
- Vulnerability Management & Reporting
- turingsecure can classify, prioritize and identify all vulnerabilities related to application security. All findings are presented graphically for better insight. A management summary, vulnerability details and remediation steps can be exported in PDF and machine format.
Linkable in Your Website
Certification with Seal
We have developed an effective and comprehensive format for verifiable security that can be integrated directly into your website. This certificate proves to third parties such as customers or insurance companies a high level of security, data protection and IT security awareness.
The certificates we issue prove a high level of IT security at a given time according to a standard or individual test modules. Depending on the assessment, different test guidelines are chosen and evaluated.

Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment: