Cloud Cyber Security
Due to the increasing complexity of cloud infrastructures, many services are misconfigured. We help you identify and eliminate misconfigurations and their impact on cloud security.
Definition and Explanation
What is a Cloud Security Assessment?
In a cloud security assessment, a cloud infrastructure is analyzed and evaluated. The various configurations in terms of identity and user rights are very different from traditional infrastructure. Our procedures are specifically designed to address these needs and effectively identify configuration and implementation errors. Any identified security issues are presented to you along with an impact assessment, risk elimination proposal or technical solution.

Cloud IT Security with Pentests
How do you Verify the IT Security of a Cloud?
Almost all cloud providers promise to be very secure and to preserve data in the best possible way. Home office and remote work are just one driver in cloud usage. Whether for personal or business use, everyone has had to deal with a cloud service at some point. Access is via an Internet-enabled device, such as a smartphone or laptop. These devices may have previously been infected with a virus and thus also infect the cloud. Thus, the IT security gaps and attack vectors in a cloud are also different. To identify these gaps and the faulty configurations and eliminate them later, a so-called cloud pentest is performed.
Security and Penetration Testing
Cloud Penetration Testing for more Cyber Security
Penetration testing for cloud configurations is planned, executed and evaluated by our specially trained security engineers according to recognized cyber security standards.
- Extensive Reporting Format
- Our report is prepared according to recognized standards and contains, among other things, a management summary, a vulnerability overview, details of the vulnerability, and remediation steps. The assessment of the findings is based on the CVSS 3.0 standard.
- Certification as Proof for your Customers
- Use our comprehensive security certificate to prove to customers the high security level of your applications and infrastructures. Successful accreditation is preceded by a cloud assessment or penetration test.
- Implementation according to Recognized Standards
- We offer the following test standards: OWASP and CIS Benchmark. Depending on the information base, we perform white, grey or black box tests

Cyber Security in der Cloud
Boutiqe Consulting with Expertise in Cloud Cyber Security Assessments
We offer all services in various complexities and recognized standards.
- Identity and Access Management
- Analyze permissions for privilege escalation paths and check for misconfigured roles and unauthorized access attempts.
- CIS Benchmark
- CIS benchmarks are among the best practices you can use to configure a target system securely. They therefore support you in making your IT systems, networks, software as well as cloud infrastructure secure.
- OWASP Cloud Testing Top 10
- With the OWASP Cloud-Native Application Security Top 10, we test organizations looking to securely adopt cloud-native applications. This guide includes the top attack vectors for the cloud.

Levels of Abstractions
Depth of the Cyber Security Assessment
- Cloud Configuration Management
- The various configurations in terms of identity and user rights are very different from traditional infrastructure. Our approaches are specifically designed to address these needs and effectively identify the configuration and implementation errors.
- Self-managed Infrastructure
- We help you audit your networks and protect assets. From mail servers to firewalls testing - we find the vulnerabilities in your systems!
- Compliance Checks of the Self-managed Infrastructure
- In IT security, there are many guidelines that must be adhered to. In case of non-compliance, these usually do not represent a vulnerability in the classical sense. We check existing compliance guidelines or adapt our security recommendation for your company.
The 3 most Common Providers
Our Services in the Area of Cloud Security Assessment
We offer cloud security auditing for the following cloud providers.
Amazon Web Services
One of the strongest features of AWS is the immense flexibility offered to the user in setting up the environment. This flexibility is great, but it also presents a major security problem. A pentest of the AWS cloud infrastructure can be used to find these security issues.
Google Cloud Platform
GCP provides a shared responsibility model where the customer is responsible for security, such as server configuration and privilege implementations granted in the environment. We identify faulty configurations in the GCP pentesting.
Microsoft Azure
Azure comes with a number of security features for experienced users. While this is a good start, it is the responsibility of each user to maintain their stability and security. With an Azure Pentest, we check the security of the cloud provider's configuration.
Range of Services for Cyber Security
Further useful Services within the Scope of an IT Security Audit
- Penetration Test
- Penetration tests are simulated attacks from external or internal sources to determine the security of web applications, apps, networks, and infrastructures and uncover any vulnerabilities.
- Phishing Simulation
- A spear phishing simulation is used to increase the detection ability of employees. We help you to sensitize your employees and thus strengthen the last barrier.
- Static Code Analysis
- Static code analysis, also known as source code analysis, is typically performed as part of a code review and occurs during the implementation phase of a Security Development Lifecycle (SDL).
- Red Teaming
- Red Teaming is used to test an organization's detection and response capabilities. Our Red Team tries to access sensitive information in every possible way and as undetected as possible.
Process steps of Cloud Security
Cloud Security Procedure
The assessment we perform is an agile process and is carried out in close consultation with the customer.
Kick-off
During a joint kick-off meeting, the framework conditions to be tested are specified, necessary user accounts and access paths are coordinated, contact persons and escalation paths are defined, and the pentest is planned together in detail.
Manual & Automated Research
Our security engineers try to gather as much information as possible. Based on this information, analysis strategies are developed to identify possible attack vectors. These attack vectors are then examined for vulnerabilities in extensive tests.
Manual Exploitation
Here, an attempt is made to exploit the identified vulnerabilities to gain access to the target systems. In the process, our pentester writes new exploits or uses existing ones, depending on the service or technical environment in question. Potential vulnerabilities can turn out to be false positives here. Only verified vulnerabilities are included in the final report and classified according to their criticality according to CVSS 3.0.
Report
We have developed a comprehensive report format that provides optimal insight into our work and its results. This consists of a business risk analysis, management summary and a comprehensive test and vulnerability description. The criticality of the vulnerabilities and recommendations for action are described in detail therein.
Final interview & Certification (optional)
When the analysis is complete, then the remediation of the identified vulnerabilities takes place on your part. Our evaluations provide you with detailed recommendations about the vulnerability in question. If needed, our security engineers can provide extensive remediation assistance.
Remediation (Optional)
In the final meeting, all critical points in the results report are discussed and all questions are clarified. Finally, we will gladly present you with a certificate as proof for your customers.
Free review (Optional)
We are happy to review the security weaknesses again to ensure that the defense mechanisms have been implemented correctly. It is important to us that our recommendations are implemented, which is why this process activity is always free of charge.
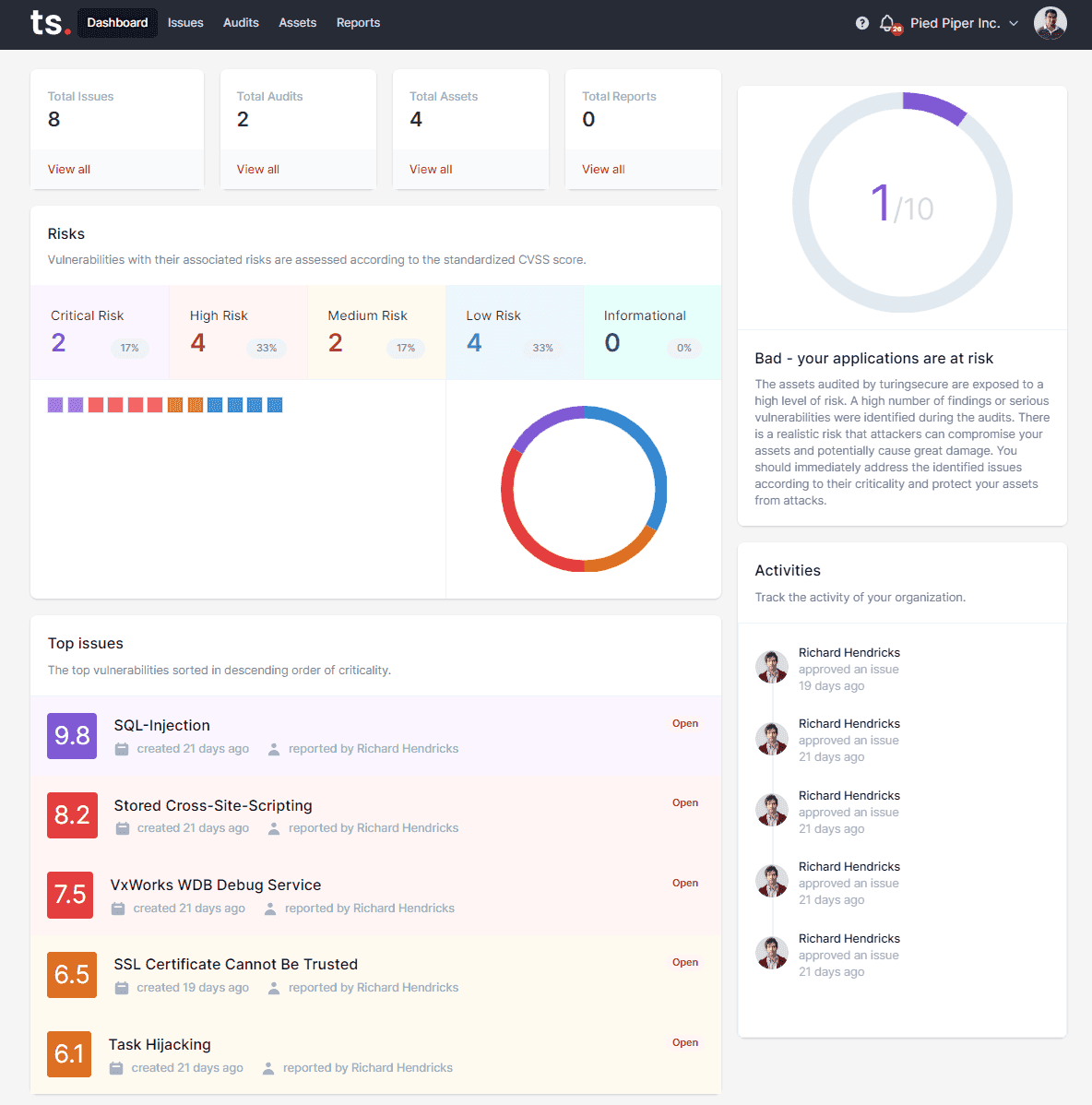
Penetration Testing as a Service (PTaaS)
Penetration tests on the platform turingsecure.
We offer comprehensive vulnerability management for customers, partners, penetration testers and IT security consultants. Use our software products to also get the best technologies and reporting tools on the market.
Comprehensive Solutions for Your Application Security
With our comprehensive and intuitive platform, you can now map the entire security process of your applications.
- Continuous Application Security Testing
- Continuous Security Application Testing (CAST) ensures that applications are tested for vulnerabilities in a regulated cycle. Our methodology allows direct integration into the agile development process and thus enables a high continuous security level.
- On-Demand Penetration Testing
- Application penetration testing is scaled as needed to meet the more complex requirements. For a sophisticated application, a quick and manual penetration test can be performed to identify vulnerabilities in the business logic of your application.
- Vulnerability Management & Reporting
- turingsecure can classify, prioritize and identify all vulnerabilities related to application security. All findings are presented graphically for better insight. A management summary, vulnerability details and remediation steps can be exported in PDF and machine format.
Linkable in Your Website
Certification with Seal
We have developed an effective and comprehensive format for verifiable security that can be integrated directly into your website. This certificate proves to third parties such as customers or insurance companies a high level of security, data protection and IT security awareness.
The certificates we issue prove a high level of IT security at a given time according to a standard or individual test modules. Depending on the assessment, different test guidelines are chosen and evaluated.

Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:













