Classification of Pentests According to BSI
Penetration tests, penetration testing or pentest(ing) for short, differ not only in the object of investigation (web, mobile, infrastructure, etc.) or depth of testing. There are six criteria that can influence the implementation of a pentest.

Table of content
Are you considering carrying out a penetration test but don't know where to start? We are happy to recommend the study on the implementation concept for penetration tests from the Federal Office for Information and Security (BSI). This is because the BSI has classified penetration tests.
Depending on the objective and its individual risk situation, a client can use criteria to determine how the penetration test should be carried out. You can ask yourself the following questions:
- Object of investigation: Which target system/application should be attacked?
- Information basis: Will access data, information such as API documentation or other information be provided for the penetration test?
- Aggressiveness: Will a test system be provided for the penetration test or do we always have to assess the effects of our actions and, if necessary, consult with the client in order to avoid disruptions to the production system?
- Location: Should the investigation take place on site or remotely?
- Objective: Should sensitive data, such as access codes, be elicited from employees by pretending false facts?
These questions and the following BSI classification should serve as food for thought for your pentest project.
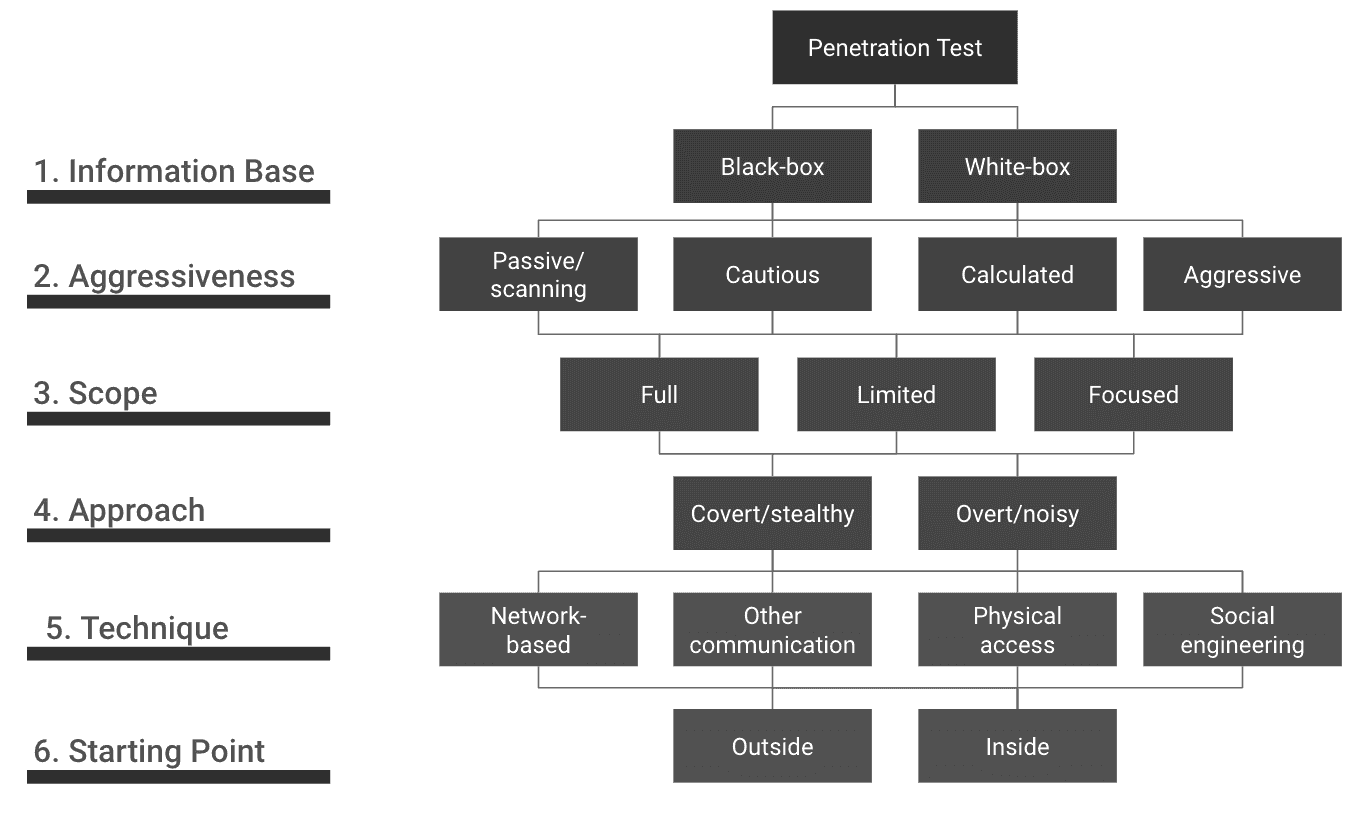
The figure provides an overview of the BSI's classification of penetration tests.
Now Imagine the Following Scenario
You have had to give notice to your long-standing employee in IT administration. This employee has extensive knowledge of the internal structure and processes in your company. He also remembers other information well (information basis: white box). He is so angry about the treatment of his person and dismissal that he decides to take revenge (aggression level: aggressive). Having worked for the company for many years, he knows the systems and applications that are used and therefore also the weak points. He therefore has comprehensive knowledge (scope: complete to focused).
Due to his emotional reaction, he will act rashly, is also not a professional hacker and will therefore be discovered at some point (approach: obvious). He will hopefully have been deprived of all access during the dismissal, so he will only be able to attack from an external perspective (technique and starting point).
The Technique
IT Infrastructure Penetration Test
The IT infrastructure penetration test involves checking security vulnerabilities such as servers, firewalls, WLAN networks and VPN access. These tests can be carried out both for externally accessible systems via the Internet and for internal company and office networks. A detailed analysis of the Active Directory structures in Windows environments and the networking of locations, systems and accounts is also carried out.
Web Application Penetration Test
This focuses on checking SaaS applications, homepages, web stores and much more. As a rule, these applications are publicly accessible via the Internet. The tests are based on the guidelines of the Open Web Application Security Project (OWASP) and take particular account of the frequently occurring vulnerabilities in the OWASP Testing Guide. However, the tests are not limited exclusively to these.
Mobile Apps Testing
Mobile App Penetration Testing is a process for checking the security of mobile applications, or apps for short. We use the OWASP Mobile Security Testing Guide to carry out mobile pentesting. In today's digital world, where sensitive data is processed and secure interoperability between different APIs must be ensured, such an analysis is indispensable.
Social Engineering
Various methods can be used here, such as fake profiles, fake emails, phishing via Microsoft Teams or telephone calls to gain access to internal information and login data. The methods are selected in consultation with the customer and relevant internal departments (e.g. data protection, works council).
The Starting Point
External Perspective
In a pentest from an external perspective, publicly accessible areas of a network are examined via the Internet. A pentester simulates an external attacker in order to partially identify internal structures and penetrate the IT environment. The tests are carried out exclusively within the predefined test scope.
Internal Perspective
In contrast, during an internal penetration test, the testers already have access to the internal infrastructure of the network. This procedure is based on the "Assume-Compromise" approach, which assumes that an IT system or user account will be compromised at some point. The investigation therefore focuses on later phases of the attack lifecycle to enable a realistic and economical risk assessment in depth.
Information Base
If you want to learn more about the information base, please read our article on white-, black- and gray-box testing methods.
Legal Aspects
Before a pentest is carried out, the client must have agreed in writing that its systems and applications may be attacked by us as the pentest service provider. Without this consent, the tests are illegal and constitute a criminal offense. The tests may only relate to objects that clearly belong to the company being tested or for which permission has been granted through additional agreements. IT systems of third parties may not be tested without their additional consent. It is therefore advisable to contractually regulate the possibility of penetration tests with third-party providers and service providers in advance or at least to clarify the procedure.
If required, we will be happy to support you with detailed explanations of the technical procedure in the event of any queries.
Sources
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
