The new OWASP Top 10 from 2021
There are three new categories in the OWASP Top 10 and the prioritization of some already known categories has changed.

Table of content
What is the OWASP?
Aims to improve the security of web applications. Through various projects (e.g. Web/Mobile Security Testing Guides, Application Security Verification Standard, and many more), as well as the numerous events, OWASP provides a repository of information that helps improve web application security. This information is backed by the extensive knowledge and experience of the contributors.
What is the OWASP Top 10?
The OWASP Top 10 is a listing of the 10 most common vulnerabilities in web applications. In addition, their risks, impact and mitigation measures are also listed. The OWASP Top 10 is updated every three to four years. The list serves as a basis for companies to plan and implement adequate security measures for web applications. However, it should be noted that the OWASP Top 10 only provides an overview of the most common vulnerabilities, so it should not be considered simply a checklist.
Comparison 2017/2021
In a nutshell, there are three new categories and the prioritization of some already known categories has changed. In addition, some previously listed vulnerabilities have been combined into larger categories.
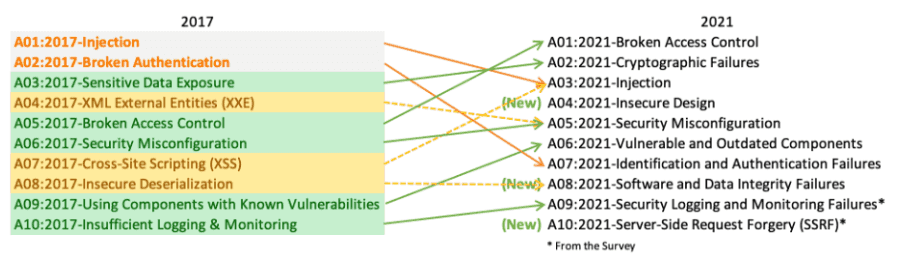
The biggest change, however, is in how the OWASP Top 10 should be viewed. While the original focus of the Top 10 was on vulnerability classification, the latest edition takes a much more strategic approach. Most categories are now broader than before, covering more areas. And while the top 10 are still data-driven, they are no longer categorized primarily by frequency - instead, the focus is on vulnerability exploitability and impact.
The top 10 now also includes two categories that were not directly gathered through statistical data, but rather through surveys of industry experts. This is to ensure that vulnerabilities that are currently not as present, but are considered important by experts, are also represented in the top 10.
Broken Access Control
The new No. 1 issue in the OWASP Top 10 is broken or faulty access controls. While the attacker comes through the front door in an authentication attack, he climbs through the open window right next to the front door in a faulty access control attack. As should be evident by the example, it is necessary to implement access controls and ensure that they work properly. Access controls restrict user privileges and ensure that sensitive information is protected from unauthorized access.
Crypthographic Failures
In the old edition this category is known as "Sensitive Data Exposure", however this describes the consequence rather than the real underlying cause. Therefore, the name has been changed to reflect that the focus is on encryption errors, which in turn can lead to exposure of sensitive data. Sensitive data includes, but is not limited to, passwords, credit card numbers, health records, personal information, and trade secrets that require special protection, especially if that data falls under privacy laws.
Injection
The category of injections has dropped from first to third place. This is due in part to the implementation of protections in the frameworks used by developers or even new languages. In addition, cross-site scripting vulnerabilities now also belong to this category. An application is generally vulnerable to injection attacks if user-supplied data is not validated, filtered or sanitized by the application.
Insecure Design
Insecure design is a new risk category that focuses on risks associated with design flaws. It is a broad category that encompasses many different vulnerabilities. This is about ensuring that the application is designed securely from the very first steps. This can be achieved through threat modeling workshops, adherence to basic "security by design" principles, and the use of reference architectures.
Security Misconfigurations
Security misconfigurations have risen one place from the previous top 10 and now additionally include the category of "XML External Entities (XXE)". Misconfigurations occur, for example, when the default configuration is taken over unchanged.
Vulnerable and Outdated Components
Formerly also known as "Using Components with Known Vulnerabilities", includes any software that contains vulnerabilities, is no longer supported, or is also outdated. If the version numbers of components, including all direct and indirect dependencies, are not known and components are not subjected to regular security scans, one is at risk.
Identification and Authentication Failures
This category originated from the Broken Authentication category and dropped from second to seventh place. According to OWASP, it is still a major component of the top 10, but the number of frameworks available today greatly reduce the risk. A security risk exists when a user's identity, authentication or session management is not handled properly, allowing attackers to exploit passwords, keys, session tokens or implementation flaws to temporarily or permanently take over a user's identity.
Software and Data Integrity Failures
Another new category is that of "Software and Data Integrity Failures," which refers to the lack of proper integrity checks for software updates, critical data, or the CI/CD pipeline. Furthermore, the category of "Insecure Deserialization" has been added to this category.
Security Logging and Monitoring Failures
The category previously known as "Insufficient Logging and Monitoring" has been renamed "Security Logging and Monitoring Failures" to capture multiple types of vulnerabilities. Without logging and monitoring, attacks and other security breaches cannot be detected. These include brute force attacks, for example; these are detectable by many failed logins in a short period of time.
Server-Side Request Forgery (SSRF)
Server-Side Request Forgery is a category that was added as a result of the industry survey. According to the OWASP survey data, the frequency of this risk was relatively low, but the potential for exploitation and impact was higher than average. SSRF vulnerabilities occur when a Web application retrieves a remote resource without validating the URL provided. They are most common in applications where users can download an asset from an external resource, such as webhooks, integrations, and PDF generators.
Conclusion
There are some significant changes in the current OWASP Top 10 list compared to 2017. While injection vulnerabilities, which were #1 for a long time, rank lower, access control flaws are increasing in importance. In addition, categories are becoming broader and less specific to include many different vulnerabilities under this hat.
Nevertheless, it must be noted that the OWASP Top 10 is not an exhaustive list of all possible security attacks on web applications. Rather, it is a guide that highlights the most common attacks on web applications.
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
