Maturity Analysis of the IT Security Organization
Every IT security organization should evaluate at which stage the measures already taken are in order to avoid redundant security analyses.

Table of content
Every IT security organization should evaluate at which stage the measures already taken are in order to avoid redundant security analyses. For this purpose it is important to define the current maturity level of the company, since the different security assessments, such as pentesting, build on each other. Often there are also legal and regulatory requirements of the relevant industry, markets or countries. It would not make sense to carry out a complex attack simulation, if no simple vulnerability scan or penetration test has been carried out before, because the chance of success is almost 100% and the corresponding findings are not meaningful.
icle, after a definition of the different levels of mat
hen does which IT security service make sense?
Technical and Organizational Measures
Technical and organizational measures (TOM) are the measures prescribed by Art. 32 of the Basic Data Protection Regulation (DSGVO) to ensure the security of the processing of personal data. All of the points described fall under the principle of proportionality, which means that service providers do not necessarily have to take the same protective measures as the client, for example. Every IT responsible person should thoroughly deal with this measure in order to create a data protection compliant and company-wide concept. For more information about TOMs, please visit IBM.
Technical Measures
The technical measures have an influence on data processing. This therefore includes all measures that guarantee IT security from the systems used to the security of the building.
Examples for this subcategory are:
- Encryption of the data medium or the data transmission
- Automatic backups
- Availability control
- Pseudonymization
- Restorability
- Input control (revision security and user identification)
- Access control
- Forwarding control
Organizational Measures
The organizational measures influence the general conditions of the technical processing. Accordingly, they represent all non-technical measures.
Examples for this subcategory are:
- Emergency Management
- Access control
- Order control
- Training of employees in data protection
- Separation monitoring
- Obligation of confidentiality of employees
- Data protection management
- Principle of dual control
IT Vulnerability Analysis
This type of security analysis is the simplest security assessment, which checks how secure the internal IT infrastructure is against external or internal attackers. It can provide a good overview of the organization's attack surface and serves as a simple means of obtaining the information needed for further assessment, such as penetration testing.
IT vulnerabilities are identified that have already been reported or are caused by outdated software. Often the risk of danger can be solved by an active and good patch management. Complex vulnerabilities cannot be found with a vulnerability check because no in-depth analysis is performed..
Penetration Test
In a pentest, the manual evaluation is in the foreground, since an automated security scan does not include complex attack chaining. Pentesting is therefore one of the more complex IT security audits, since a serious vulnerability can be created from several vulnerabilities of low criticality. Often process-related weaknesses in the business logic of web or API components are also found, so an independent check of the IT infrastructure, web applications and mobile apps is very important. A pen test always includes details of the vulnerability and detailed remediation steps for the IT stakeholders or developers.
For a high level of IT security a thorough examination of software and hardware is required!
Attack Simulation
Attack simulations, often called Red Teaming, go far beyond pure infrastructure and application security. It emulates a malicious actor actively attacking and trying to escape detection, similar to an Advanced Persistent Threat (APT). Spearphising attacks also fall into this category of attacks, as this is also a way to test the response of internal IT processes. Phishing attacks are a form of digital social engineering, which are often the starting point for lateral movement.
The goal is always to present a successful data exfiltration and an immediate threat, which should reflect the emergency. An attack simulation thus tests the IT processes and employees by actively challenging them by a malicious actor
The Maturity Model of IT Security
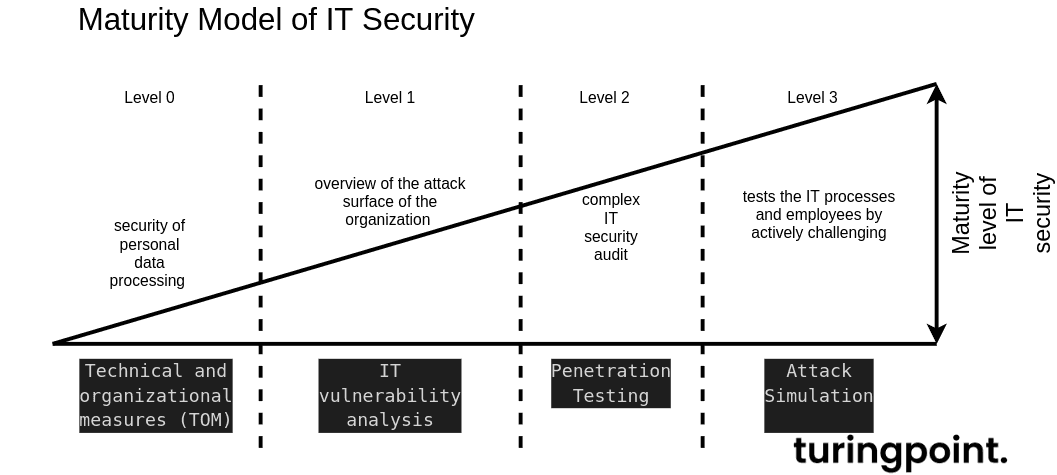
The maturity of a company or a process is compared with a development path divided into levels. A certain level is reached depending on the capability. The values of IT security are defined in certain criteria in relation to maximum achievable states. The optimum would be if an organization could withstand a continuous attack simulation.
Conclusion
A comprehensive maturity model should be created to assess where the process or business needs to be developed and whether security standards such as IT-Grundschutz, BSI 100-x and ISO2700x are relevant. If no measures have been taken, then the setup for the technical and organizational measures should be started. Only then should a penetration test be carried out and after the implementation of the hardening measures an attack simulation. All described security assessments are part of an effective information security management with IT-Grundschutz and ISO 27001.
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
