Man-in-the-Browser Attacks
The man-in-the-browser attack is a form of man-in-the-middle attack in which an attacker takes control of the browser.

Table of content
The man-in-the-browser attack is a form of man-in-the-middle attack in which an attacker takes control of the browser and acts as a middleman between the graphical content displayed to the user and the server. This position can now be used by the attacker to intercept and manipulate the requests at will. The man-in-the-browser attack is commonly used by attackers to carry out various forms of financial fraud, usually by manipulating Internet banking services. Various forms of malware can be used to carry out the attack, usually malware referred to as Trojans. The attack can be very difficult for a standard user to detect, as even when SSL is used, all the expected controls and security mechanisms function normally.
How does a Man-in-the-browser Attack Work?
The man-in-the-browser attack is usually a Trojan malware that is executed in a specific process. In most modern web browsers, this is a specific tab. Now, when the victim browses the Internet, the malware is attached to these tabs. The three most common attack vectors are:
Compromised Browser Extensions
Browser extensions are modules to extend the usability of a browser and customize its use. For example, extensions can read cookies and other data, manipulate DOM elements, and make POST and GET requests. Since most modern extensions are also source-only, they may also have vulnerabilities that can be exploited by a attacker to inject malicious code.
API Hooking
Browsers rely on operating system APIs and DLLs to function properly. For example, a web browser for Windows may rely on the wininet DLL to send and receive HTTP requests. Malware can alter the API flow to act as a "man-in-the-middle" between the API and the requesting process, giving them extensive control over the functionality of the process.
Vicious Content Scripts
Content scripts are script files that are executed in the context of a web page in the user's browser. These scripts are able to read and manipulate web pages by using the Document Object Model (DOM). Malicious content scripts can be injected into web pages by either infecting the web page on the hosting server or using MITM techniques to infect the HTTP response sent to a particular client.
Man-in-the-Browser Attack Example
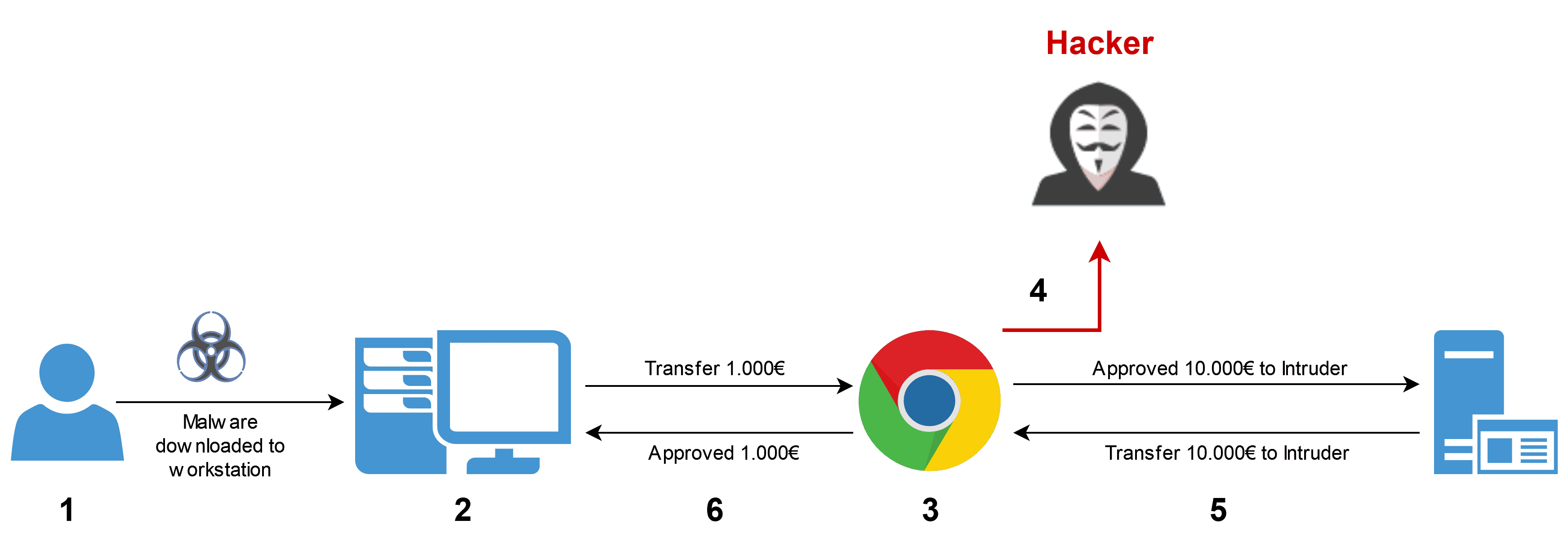
- The victim's computer is infected with a MITB Trojan through a form of social engineering attack
- The Trojan infects the computer's web browser
- The victim logs into their bank website to transfer money
- The malware intercepts and modifies the transaction
- The money and confirmation are sent to the attacker
- The malware sends the victim a legitimate-looking confirmation page stating that the requested transfer was successful
Reducing the Risk of Man-in-the-browser Attacks
There are several ways to mitigate the risk of a man-in-the-browser attack. One way is to restrict user rights, this makes it more difficult for an attacker to access administrator processes. However, this usually reduces the user-friendliness of the system.
User awareness is also an important factor in reducing the risk. Users should be trained to recognize suspicious browser extensions. Since there is usually no indication from the user's perspective that their browser is compromised, users should be encouraged to regularly close their browser sessions when they are no longer needed. Furthermore, users should be trained to withstand social engineering attacks.
Another effective countermeasure is to regularly update the virus scanner. Since many MITB malware programs contain static code files, they can be reliably blocked and removed by antivirus software. Furthermore, apps or software should not be downloaded from untrusted sources either.
How do I Detect Man-in-the-browser Attacks?
One of the biggest problems in dealing with MITB attacks is that they are difficult to detect. Normal user traffic masks attacker traffic, no new processes are created, and malicious logins are difficult to distinguish from normal user logins.
Still, there are subtle clues that can point to a MITB attack:
- There are additional or missing elements on the website
- You receive a login notification from a device you don't recognize
- You are logged out of the user account
- The antivirus program detects malware on the computer
Conclusion
A man-in-the-browser attack is one of the most effective ways to steal from people online. The good news is that while such attacks are difficult to detect, they are easy to prevent. A man-in-the-browser attack is not possible without installing a Trojan first. With the right security software, proper user account management and user training, companies can significantly reduce the likelihood of their employees becoming another victim of a MITB attack.
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
