Email Encryption with PGP
The purpose behind using PGP is that sent messages cannot be intercepted and read by anyone during transmission because of the encryption.

Table of content
Introduction
PGP stands for Pretty Good Privacy, but it is more than just "Pretty Good". In fact, PGP is the most widely used email encryption system. The point behind using PGP is that because it is encrypted, sent messages cannot be intercepted and read by anyone during transmission. PGP has been thoroughly tested over its many years of use, and the few weak points are known and fixed.
What is PGP?
PGP is a cryptographic method that allows people to communicate in encrypted form. When a message is sent using PGP, it is previously converted into an unreadable ciphertext. Only the recipient has the key to subsequently convert the text back into a readable message on their device.
PGP also authenticates the identity of the sender and ensures that the message has not been tampered with during transmission.
Before the use of email encryption, an attacker could theoretically read all messages. Therefore, PGP was developed in the 1990s to enable the private exchange of email and other types of messages. Today, PGP is standardized in OpenPGP and has become an important standard for email security. This, among other reasons, is why it is widely used to protect individuals and organizations.
How Does PGP Work?
PGP uses a combination of symmetric encryption (i.e., a one-time-use session key that encrypts and decrypts the message) and public encryption (i.e., keys unique to the recipient encrypt and decrypt the session key). In this article, we will limit ourselves to the basic concepts.
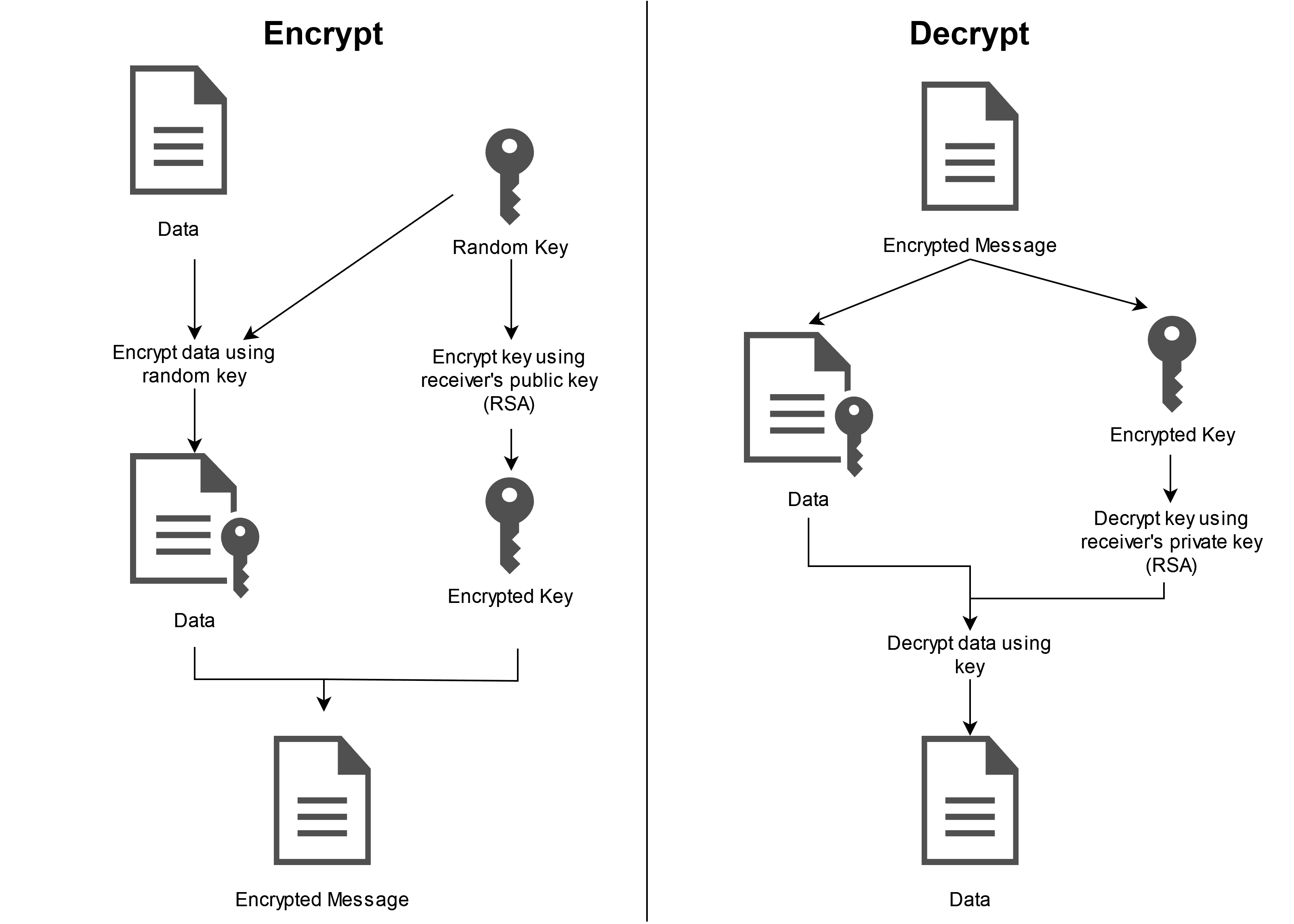
First, PGP generates a random session key. This key is a very large number that is used to encrypt and decrypt the contents of the message. Only someone who knows the session key can read the message. Since the session key is extremely large, it is very unlikely that anyone can guess it. Moreover, this session key will never be used again for other messages.
Then, the session key is encrypted with the recipient's public key. The public key is unique to each person and is used for sharing. Since it does not change, the public key is like an email address. It is tied to one person, and anyone can use it to send that person an encrypted message.
PGP takes the extra step of encrypting the message and the session key because public key cryptography is much slower than symmetric cryptography, especially for large messages. It would take a lot of time and computing power to encrypt and decrypt large emails or files directly using the public key. Instead, public-key cryptography is used only to encrypt the session key.
Using symmetric cryptography without public-key cryptography would be less practical because the session key must somehow be securely shared with the recipient. Sharing the session key in plain text would not be secure because anyone who intercepts the session key can read it and thus decrypt the entire message.
Sharing the session key over another encrypted channel or in person would be impractical for online communications. Therefore, PGP combines the efficiency of symmetric encryption with the utility of public key encryption.
Signature
The public key has one more function, signing emails or verifying the signature of an email. For example, if an email recipient is not sure who is sending them an email, they can use a digital signature in conjunction with PGP to verify the identity.
The signature uses a hash algorithm to generate a hash value. This is then signed with the sender's private key. The generated signature is appended to the message.
The signature is verified using the sender's public key. The public key is used to determine the encrypted hash value and compare it with the hash value of the message. If these values are not identical, the recipient knows that a character in the message was changed during transmission. This provides information about whether the sender is who he claims to be, whether a forged digital signature was used, or whether the e-mail message has been manipulated or hacked.
Web of Trust
In comparison to S/MIME, PGP does not have a central certification authority that confirms the trustworthiness of a key; PGP relies on users trusting each other. For this purpose, it is necessary that each PGP user authenticates the public keys of the persons he trusts with his private key. This means that a PGP user confirms that the public key of another PGP user actually belongs to that person.
Mutual authentication creates a mutual network of trust, the so-called "Web of Trust".
How Secure is PGP?
In principle, PGP is considered secure when it comes to encrypting e-mail, but this does not apply to the metadata of an e-mail such as sender, recipient, subject, date, IP address, etc.
The difficulty with PGP is more on the user side, because a user has to take care of the key management by himself and has to build up a "web of trust" by himself. The security of PGP is based on the secrecy of the private key, as well as the associated password. PGP is only secure as long as this information is kept secret and not accessible to others.
Furthermore, it is advisable to use as long a key as possible to make cracking the encryption as time-consuming as possible.
Disadvantages of PGP
The biggest disadvantage of PGP is the ease of use, which means that using PGP can lead to a lot of extra work. Moreover, users should be aware of how PGP works so that no vulnerabilities arise from its incorrect use.
Both the sender and the recipient must use compatible versions of PGP, otherwise the content cannot be decrypted by the recipient and the message cannot be read.
Conclusion
In principle, the encryption of e-mails with PGP is recommended, as the method is still considered secure. However, it should be noted that both communication partners must use PGP to be able to read encrypted messages.
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
