Differences between CVSS V3.1 and V4.0
On November 1, 2023, the Common Vulnerability Scoring System Version 4 (CVSS v4) was officially introduced as an update for version v3.1.
Table of content
On November 1, 2023, the Common Vulnerability Scoring System Version 4 (CVSS v4) was officially launched into general availability, following a period of public preview and feedback. This launch was orchestrated by the Forum of Incident Response and Security Teams (FIRST) and marks a significant update to the CVSS standard, which was last revised over eight years ago with the release of CVSS v3.0 in June 2015. The goal of this latest version, CVSS v4, is to provide improved accuracy in vulnerability assessment for industry and the public.
This new version includes several refinements, including a more detailed breakdown of baseline metrics to provide a more nuanced understanding and assessment of vulnerabilities. In addition, CVSS v4 has introduced new nomenclature to denote combinations of baseline metrics, threat and environment metrics, as well as new baseline metric values for user interaction categorized as either passive or active. For a more in-depth look at these changes, please refer to our detailed blog article.
The success of CVSS v4 depends on widespread use by the cybersecurity vendor and community, the clarity and ease of use of its refined metrics, and accurate assessment of vulnerabilities. Integration with existing systems, vendor support and active community and regulatory involvement are critical. Its effectiveness in the real world, along with a feedback mechanism for continuous improvement and timely updates in response to emerging threats, will determine its long-term impact and usefulness in improving cybersecurity measures.
What's New in CVSS v4.0?
Terminology
The CVSS framework has always consisted of three metric groups, namely Basic, Temporal and Environment. However, due to the popularity of the CVSS base value, it became synonymous with the overall CVSS value. However, the CVSS value is not just a base case. To emphasize this, CVSS v4 introduced the following new nomenclature:
- CVSS-B: Base metrics
- CVSS-BE: Base and Environmental metrics
- CVSS-BT: Base and Threat metrics
- CVSS-BTE: Base, Threat, Environmental metrics
New Base Metric: Attack Requirement (AT)
The new metric for Attack Requirement (AT) aims to provide a more detailed view of Attack Complexity (AC). This new metric captures the prerequisites and execution conditions or variables of the vulnerable system that enable the attack.
- Attack Complexity - Reflects the effort required to develop exploits to bypass or overcome defensive or security-enhancing technologies (defensive measures).
- Attack Requirements- Reflects the requirements of the vulnerable component that enable the attack.
Supplemental Metric: Supplemental Metric Group
CVSS v4.0 introduces a new optional metric group called "Supplemental Metric Group ". It provides metrics that describe and measure additional extrinsic characteristics of a vulnerability. The goal of the Supplemental Metric Group is to provide contextual information that users can use to take additional actions to assist with risk analysis. It is important to note that supplemental metrics are optional and have no impact on the calculated CVSS values. Supplemental metrics help you better understand extrinsic vulnerability issues, such as:
- Security: does exploiting this vulnerability impact an organization's security?
- Automation: Are attackers able to automate the exploitation of this vulnerability?
- Recovery: Are the systems/components able to recover themselves after an attack?
- Urgency: How high does the manufacturer rate this vulnerability?
- Value intensity: What resources does the attacker gain control of with a single exploitation event?
CVSS v3.1 vs CVSS v4.0
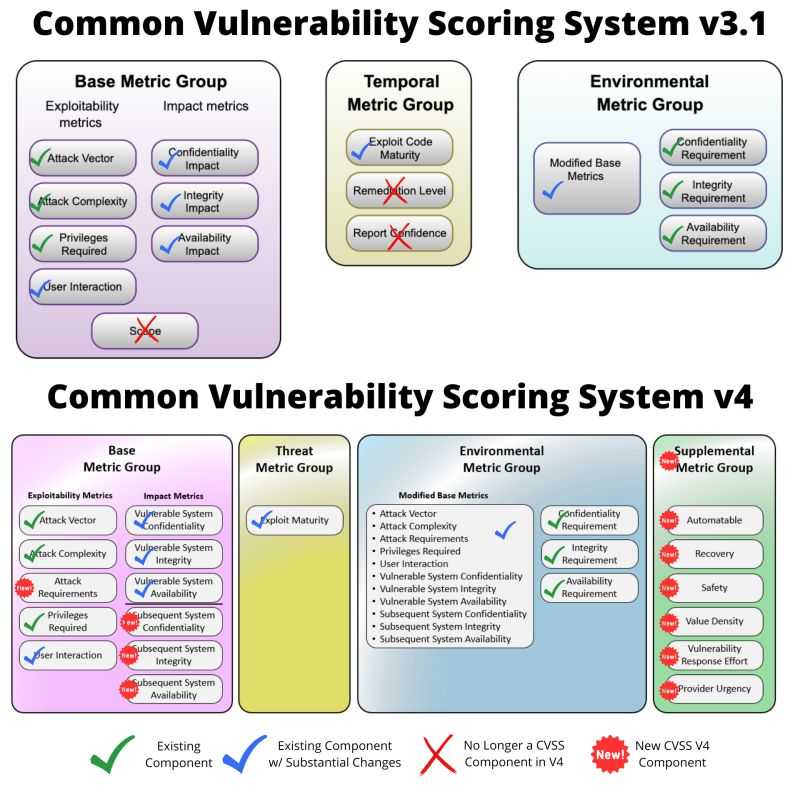
The figure below gives an overview of the changes between CVSS v3.1 and CVSS v4.0.
What has Been Updated in CVSS v4.0?
CVSS v4.0 provides improved guidelines for CVSS analysts to produce consistent scores, guidelines for assessing vulnerabilities in software libraries, etc. CVSS v4.0 is designed to support multiple CVSS scores for the same vulnerability affecting multiple platforms, products, and operating systems. It also provides guidelines for extending the CVSS framework to other industries such as data protection, privacy, and the automotive industry.
Renaming and Simplified Threat Metrics
CVSS v4.0 has renamed the "Temporal Metric" from CVSS v3.1 to "Threat Metrics". In addition, the metrics "Remediation Level (RL)" and "Report Confidence (RC)" have been abolished in CVSS v4.0. Furthermore, the "Exploit Code Maturity (E)" has been renamed "Exploit Maturity (E)". The values "High (H)" and "Functional (F)" for this metric in CVSS v3.1 have been merged into one value of "Attacked (A)" in CVSS v4.0.
Updated Base Metric: User Interaction (UI)
This metric captures the requirement that a user, other than the attacker, participates in the successful compromise of the vulnerable component. CVSS v4.0 proposes to make the User Interaction (UI) more granular. CVSS v3.1 had the values None (N) or Required (R) for the user interaction metric. With CVSS v4.0, this metric now offers more granularity in terms of required interaction, either Passive (P) or Active (A).
Deprecated Base Metric: Scope (S)
One of the CVSS v3.1 base metrics for Scope (S) was retired in CVSS v4.0 due to the lack of clarity on the use of this metric. This led to inconsistent assessments of vulnerabilities by different vendors of products. For this reason, the scope metric was retired in favor of two different impact metrics:
- Vulnerable System Impact - Confidentiality (VC), Integrity (VI), Availability (VA)
- Subsequent System(s) Impact - Confidentiality (SC), Integrity (SI), Availability (SA)
Assessment of Vulnerabilities in Software Llibraries
New guidelines explain how to assess the impact of a vulnerability in a library.
Guidance on the Use of Environmental Security Requirements Metrics
The Environmental Metric Group includes three metrics for security requirements: Confidentiality Requirement for the Vulnerable System, Integrity Requirement for the Vulnerable System, and Availability Requirement for the Vulnerable System.
Sources
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
