Budgeting in Web Application Security
IT security can never be perfect, therefore a cost-efficient approach to an optimum must take place.

Table of content
Foreword
In recent years, cyber attacks have become more targeted, complex and professional, and the technical requirements for a successful cyber attack have decreased. Many attacks are economically or politically motivated and are structured and organized by whole teams.
ngers, technical measures must be planned with a suitable budget. This article examines the IT security cataloguing and its percentage budgeting of application security in the context of web development.
Efficient security measures in application security are essential for functional application security, which includes a thorough search for errors in business logic and implementation vulnerabilities in applications of all kinds, from large cloud based solutions to web and mobile applications.
General Budget Development in IT security
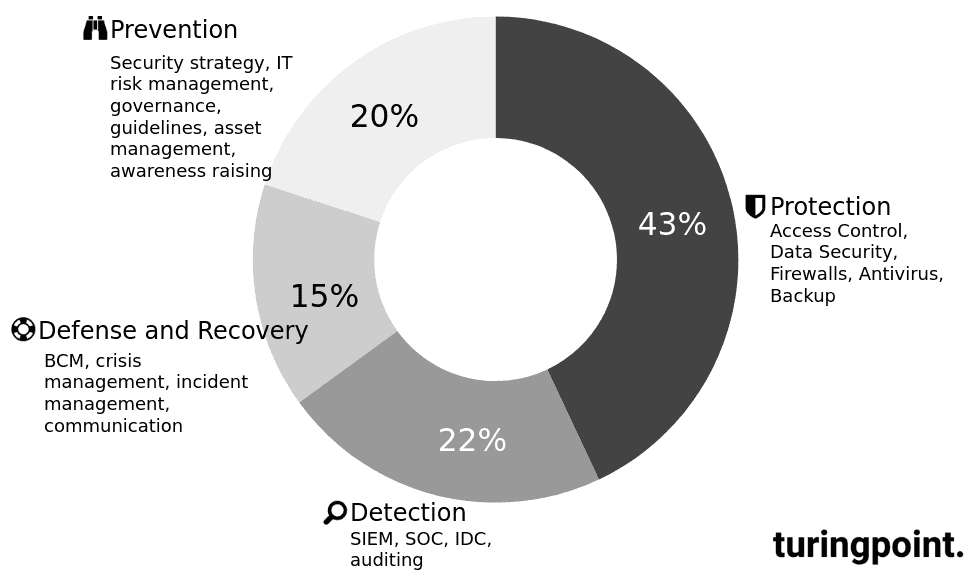
It is important that organizations spend a significant portion of their entire IT budget on information security to have the financial resources to improve their defenses and combat security breaches. It is important not to underestimate the scale of vital investment in information security and consider it an important part of the business. The budget composition of the participating companies is shown in Figure 1. Given the current threats and cyber security trends, we believe that organizations continue to devote too little attention to the issue.
i Invent study asked all participants in 2018 to divide their information security budget into four categories: Prevention (e.g. security strategy, IT risk management), protection (e.g. access control, data security), detection (e.g. SIEM, SOC) and response & recovery (e.g. BCM, crisis management). On average, contributors spent 20% on prevention (25% in 2017), 43% on protection (
Finally, the distribution of participants between internal (e.g. own security personnel) and external (e.g. service providers) information security resources was analysed. In all sectors, most participants spend the same part of their budget on internal and external resources. This budget distribution also shows that the market for security talent is currently highly competitive.
Kaspersky's IT Security Budget Calculator
Kaspersky provides a budget calculator to help companies calculate an optimal budget for the given size and industry to be efficiently positioned. The principle here describes constantly growing expenditures, as the information technology becomes more and more complex and regulatory measures lead to additional expenditure like e.g. the DSGVO.
to Kaspersky's IT Security Budget Calculator
Budgeting for Penetration Testing
In the above study, participants invested 22% of their information security budget in detection. This category includes both manual and automated penetration testing. These efforts are also in line with our recommendations, where each organization must be evaluated individually. This protective measure should never be budgeted too tightly in order to prevent existentially threatening attacks.
Cost Progression in Relation to Efficiency in manual Web Application Security
IT security can never be perfect, therefore a degressive approach to an optimum must take place. Basically, the longer analysts examine systems, the more meaningful the results are.
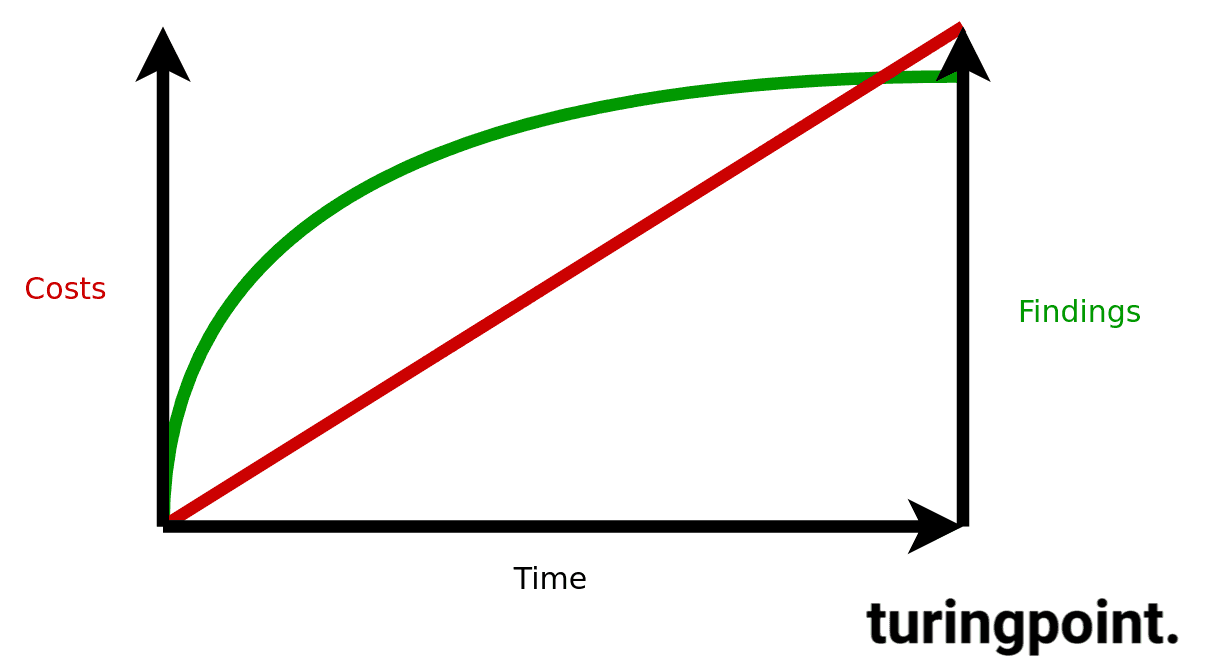
The function shown is intended to represent the process for manual penetration testing. At a certain point it is not worth to invest more time, because this only causes costs with little new knowledge. Our services offer the best possible efficiency in the functional context, so we guarantee maximum knowledge acquisition for the given budget.
Our Portfolio for Agile Web Security
We achieve a satisfactory process result among other things with turingpoints Trinity of Web Security, because here manual as well as automated tests play together in the best possible way. External expertise can be gained through cost-effective managed bug bounties.
The following article is a description of our agile methodology in web security.
Sources
Capgemini Invent, Figure 1 and budget development in IT security, September the 11th, 2019, Information-Security-Benchmark-2019
Contact
Curious? Convinced? Interested?
Schedule a no-obligation initial consultation with one of our sales representatives. Use the following link to select an appointment:
